A malvertising group nicknamed KovCoreG by security researchers has been using fake browser and Flash updates to trick users into installing the Kovter malware.
Attackers used malicious ads on PornHub to redirect users to a scam site that was advertising an urgent update. Depending on their browser, users got different messages.
For example, users arriving on this page via Chrome and Firefox were asked to download a browser update, while IE and Edge users were asked to download a Flash update.
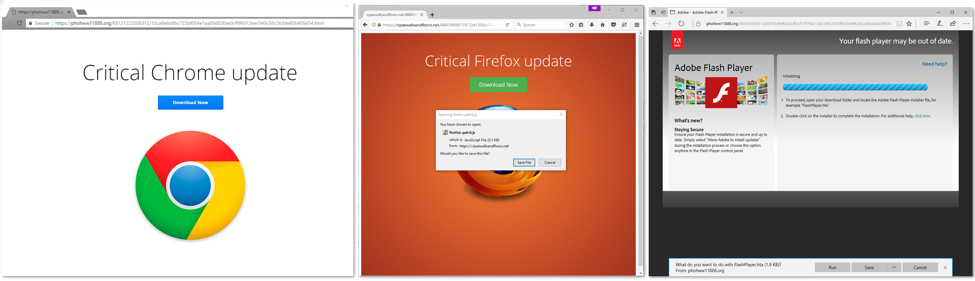
The downloadable files were JavaScript (Chrome, Firefox) or HTA (IE, Edge) files that installed Kovter, a multi-purpose malware downloader that can deliver ad fraud malware, ransomware, infostealers, or more.
Campaign focused on UK, US, Canadian, and Australians
Researchers from Proofpoint discovered this malvertising campaign and informed both Pornhub and Traffic Junky — the ad network's whose ads were being abused. Both companies intervened and shut down the ads, but researchers expect the group to pop up somewhere else online. [UPDATE: The campaign is now on Yahoo's sites.]
This particular group fits recent malvertising trends where the malvertisers focus on redirecting users to social engineering (scam, fake download) sites, instead of sending users to exploit kits.
The KovCoreG used ISP and geographical-based filters to separate only the users they wanted to attack. The PornHub campaign targeted US, UK, Canadian, and Australian users.
Researchers noted a curious thing about this campaign. The downloaded files — the JavaScript and HTA files — wouldn't execute on a computer if the PC's IP address didn't pass the same ISP and geo filters. The purpose of this second check was to limit analysis from security researchers.
Two weeks ago, security researchers from Malwarebytes discovered a similar malvertising campaign on MSN.com, with malicious ads delivered from the Taboola advertising network. The ads would redirect users to tech support scams.
Reports on the KovCoreG and Taboola malvertising campaigns are available here and here.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now