As more and more ransomware outbreaks are discovered, the line has become blurred in whether they are being utilized as a wiper or an actual ransomware. Such is the case with a new ransomware attack called ONI that has been used in targeted month long attacks against Japanese companies.
ONI goes phishing
It all started when security firm Cybereason analyzed some computers that were infected with a ransomware called ONI. This ransomware has been analyzed before, but it was not understood how the ONI victims were being infected. After analysis by Cybereason researchers, it was discovered that the infected computers had also been previously targeted by a spear phishing campaign that installs a RAT, or Remote Access Trojan, on the victim's computer.
These phishing emails pretend to be receipts that contain a zip attachment with a malicious Word document inside it. When a user opens the document and enables macros, a VBScript script will be launched that downloads and install a copy of the Ammyy Admin RAT onto the infected computer.
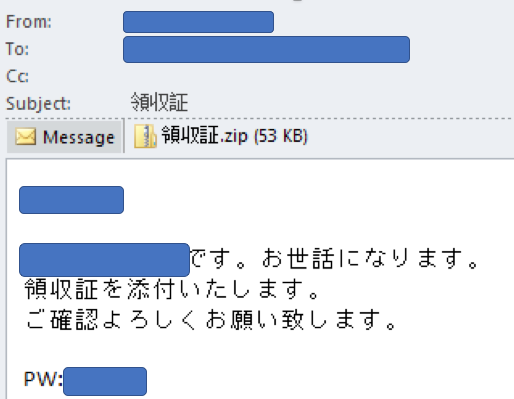
Source: Cybereason
While Ammyy Admin is a legitimate remote administration tool, in this case it is being used by the attackers to gain full access to the system. According to Cybereason, they have found instances of this RAT being installed as far back as December 2016 and as recently as September 2017.
Cybereason has told BleepingComputer that all of the targets were medium-large companies and there have not been any reports of government related incidents.
Covering their tracks
Once the attackers were able to gain access to a network, they further worked on gaining access to the domain administrator account and servers. Unfortunately, at this point it becomes a bit fuzzy as to what the attackers were doing during their three to nine month access to the hacked network.
Cybereason has told BleepingComputer that "it's safe to assume that sensitive data was exfiltrated during those months of active hacking operation".
When the attackers were finished with their hacking operation, ONI Ransomware would come into play. As the attackers had access to the domain servers, they would utilize Group Policy Scripts to execute a batch file that cleaned up over 460 different event logs in order to cover their activities.
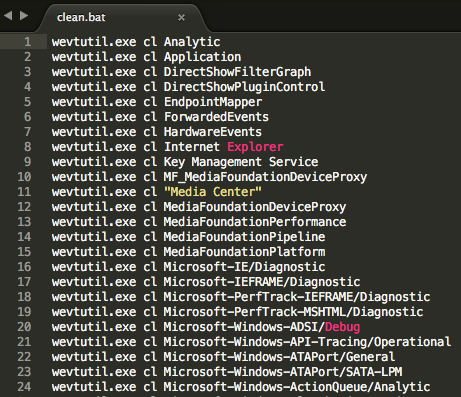
Source: Cybereason
This same script would also deploy the ONI ransomware on computers in order to encrypt files and to possibly further obfuscate the activities of the attackers.
ONI Ransomware: A Ransomware or a Wiper?
An interesting aspect of this attack was that the attackers used two different versions of the ONI Ransomware. One version, which was used to mostly target non-critical computers, is a GlobeImposter variant that acts as a user mode encryptor.
When installed, ONI Ransomware would encrypt the computer's files and append the .oni extension to encrypted files as shown below.
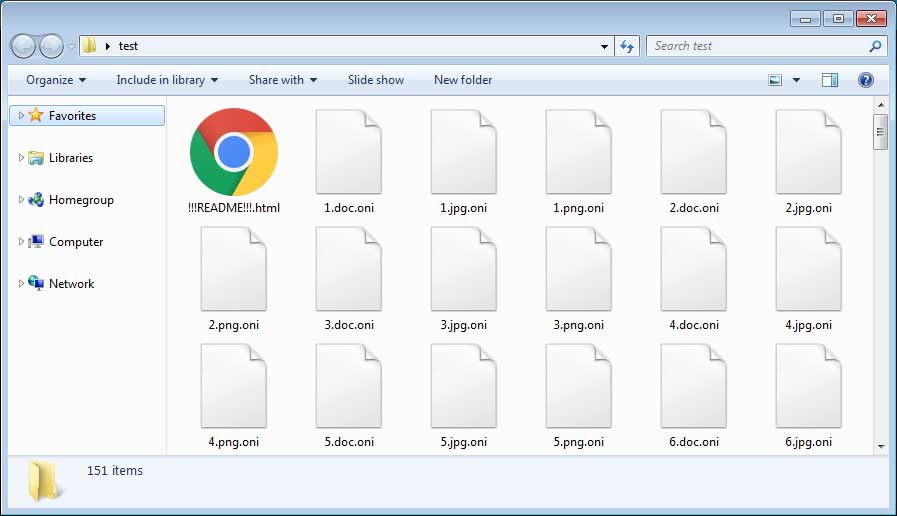
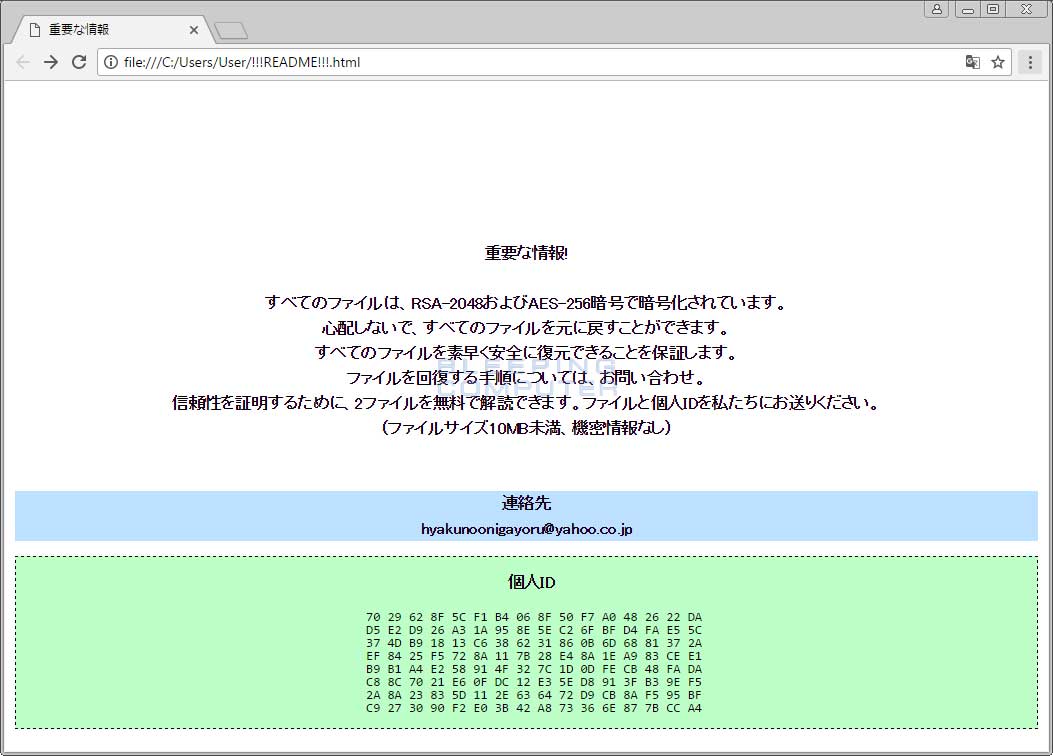
When done, victims would then find a ransom note named !!!README!!!!.html located in folders where files were encrypted. These ransom notes contain basic information on what happened to the victim's files and an email that can be used to contact the attackers for payment instructions.
This is all standard procedure for GlobeImposter ransomware variants.
It gets more interesting, though, when Cybereason discovered that the attackers were also using another ransomware on certain computers. This ransomware is being called MBR-ONI because it encrypts the actual as it encrypts the actual file system and then replaces the MBR, or Master Boot Record, with a password protected lock screen that is displayed before Windows boots.
It does this by utilizing the legitimate DiskCryptor program, which was recently used by the Bad Rabbit Ransomware attack, to encrypt the file system and requires a password to make it accessible again.
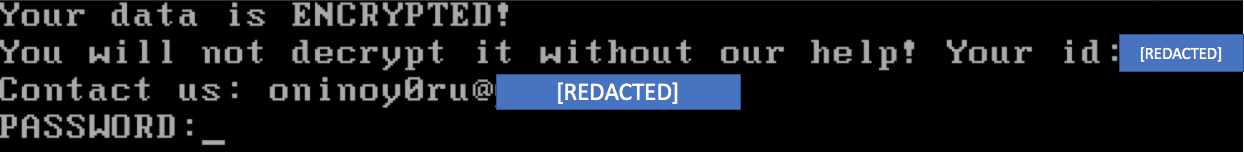
Source: Cybereason
According to Cybereason, MBR-ONI was only deployed on active directory servers or "critical assets".
Unlike the NotPetya attack which would not allow decryption of the file system, ONI and MBR-ONI are legitimate ransomware infections that can be decrypted if the victim acquires the decryption key. While Cybereason has told BleepingComputer that there have been no reports of victim's paying the ransom or even contacting the attackers, the way these ransomware were used is not commonly done.
The question remains as to whether the attackers were using ONI to earn some extra money after they finished their attack, to make computers and files inaccessible to cover their traces, or maybe even both. Only time will tell.
IOCs
Hashes:
SHA256: 9bba34947b9b2f9d52aeb45b342637ce93d6683bbf8e352da53dae053da37ae6 (GlobeImposter Variant)
Files associated with ONI:
!!!README!!!.html
ONI Ransom Note (Japanese):
重要な情報!
すべてのファイルは、RSA-2048およびAES-256暗号で暗号化されています。
心配しないで、すべてのファイルを元に戻すことができます。
すべてのファイルを素早く安全に復元できることを保証します。
ファイルを回復する手順については、お問い合わせ。
信頼性を証明するために、2ファイルを無料で解読できます。ファイルと個人IDを私たちにお送りください。
(ファイルサイズ10MB未満、機密情報なし)
連絡先
hyakunoonigayoru@yahoo.co.jp
ONI Ransom Note (English Translation):
Important information!
All files are encrypted with RSA - 2048 and AES - 256 ciphers.
Do not worry, you can restore all the files.
We guarantee that all files can be safely restored quickly and safely.
For instructions on recovering files, contact us.
To prove reliability, you can decipher two files for free. Please send us the file and personal ID.
(File size less than 10 MB, no confidential information)
contact information
hyakunoonigayoru@yahoo.co.jp


Comments
Amigo-A - 6 years ago
'''''Ammyy Admin is a legitimate remote administration tool'''''
It should be noted that the utility Ammyy Admin and sites of the company "Ammyy" Ltd. were many, many times compromised, hacked, infected.
https://www.esetnod32.ru/company/press/center/eset-avtory-buhtrap-osvoili-apt-ataki/
https://securelist.ru/blog/issledovaniya/28900/lurk-a-danger-where-you-least-expect-it/
http://news.softpedia.com/news/ammyy-admin-website-compromised-to-spread-cerber-3-ransomware-508330.shtml
Amigo-A - 6 years ago
Cylance assert that file %Temp%\qfjgmfgmkj.tmp - special file that prohibits the re-installation of this encryptor. So it can be used for protection.